Now that we’ve been introduced to social engineering, it’s time to learn about the vulnerabilities in the system we’re trying to hack into: humans.
Social engineering is all about making someone do something that they’re not supposed to do. Like the hacker who posed as a Verizon employee and broke into the CIA director’s email. Or the guy who charmed his way into a bank vault and made off with $28 million worth of gems. Or the true story behind the movie Catch Me If You Can.
There are weaknesses in every system and humans are no exception. So let’s take a look at a few of our behaviors and tendencies that leave us open to attack.
#1 Greed
One of the most commonly exploited human weaknesses in social engineering is greed: offer people something they want. You’ve probably come across emails like this one in your spam folder:
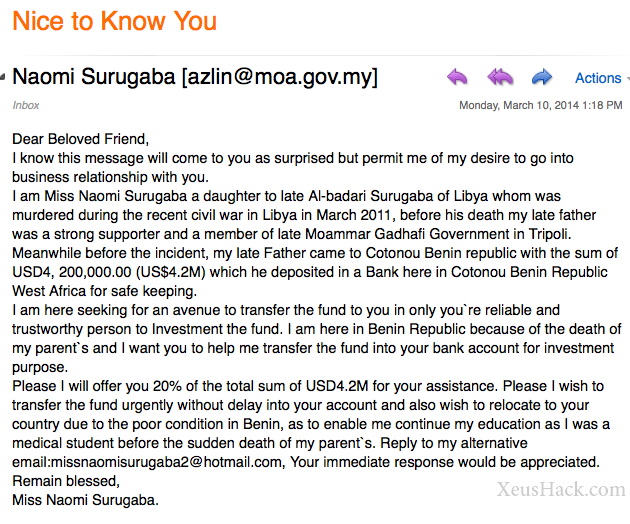
This is one of the most common types of phishing attacks. The attacker is preying on the greed of the victim. There are hundreds of variations of these kinds of attacks but they all have one thing in common: the attacker promises the victim a large sum of money in exchange for some basic details like name, age and phone number. Once the attacker obstains this, they then ask for the victim’s financial information or even try to get them to pay up directly.
. If you were thinking these types of attacks don’t happen anymore, think again. Each year, hundreds of millions of phishing emails are sent out. Of course, they are only successful against victims who are quite gullible but the numbers are on the attacker’s side. Only one out of hundreds or thousands of victims need to comply and the attacker’s endeavor can turn out to be quite profitable.
#2 Fear
Another weakness is fear. Fear can take on many forms…
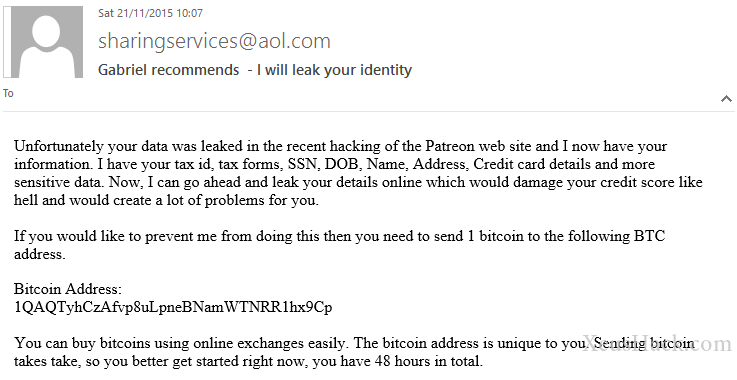
The above type of attack is getting more and more common given the recent data breaches. The attacker claims to have some very private information that he is threatening to leak unless the victim pays up. Following the Ashley Madison hack of 2015, thousands of victims received emails blackmailing the victims to hand over some bitcoins or their deepest and darkest secrets will be exposed. It is believed that the attackers made off with hundreds of thousands of dollars.
And then there’s this…
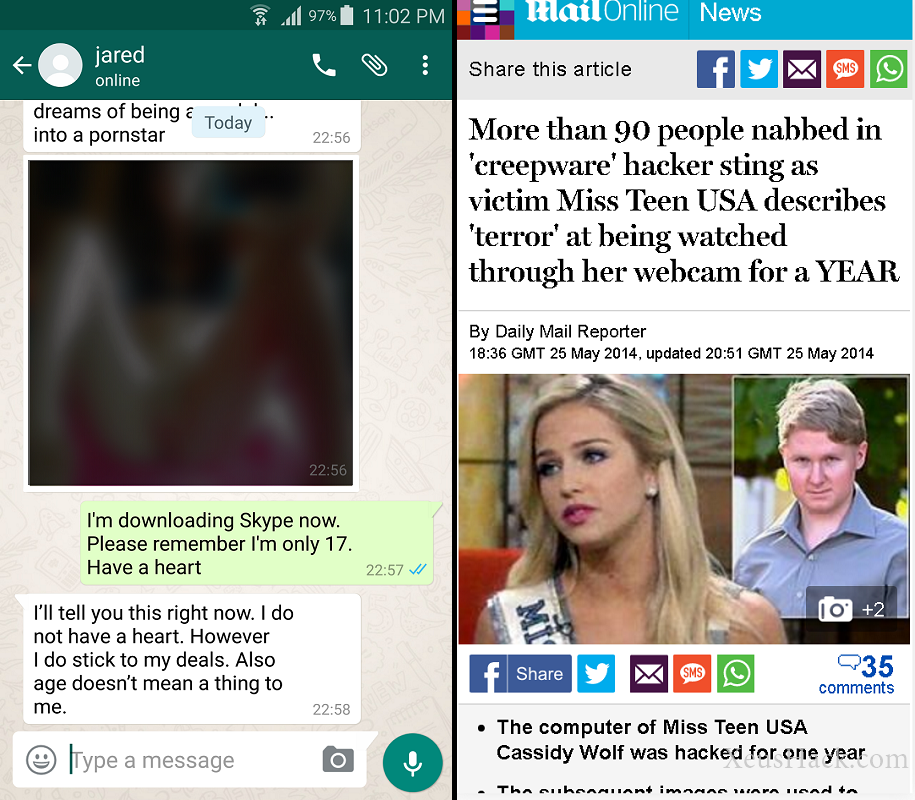
The chat screenshot you see above is the actual conversation between the attacker and his victim from this FBI report. The hacker, who was eventually charged with sextortion, broke into several girl’s computers (including Miss Teen USA) and tried to blackmail them. The fear of embarrassment lead dozens of his victims to comply.
Fear can indeed be a powerful tool and wreak havoc in the hands of a malicious attacker.
#3 Urgency
Let’s take a look at the above image once more. In particular, the last line:
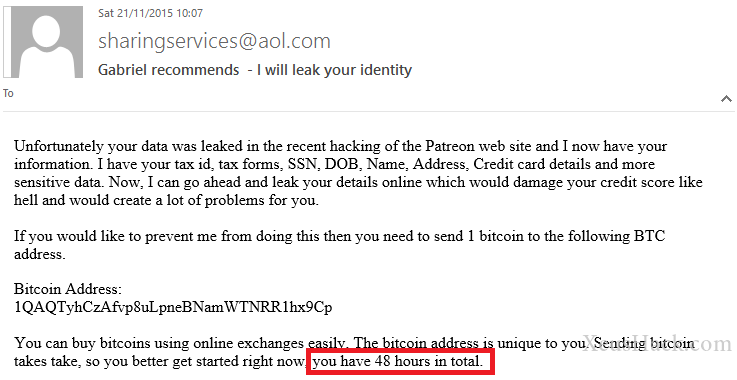
The attacker is threatening the victim to act within 48 hours or their private data will be leaked. Setting a time limit on the threat puts it into very real terms from the point of view of the victim. If they truly believe that they must obey now, they may not act rationally and give in to the demands that they otherwise wouldn’t have.
It isn’t just hackers though, the sense of urgency is actively exploited by companies and marketers to make you buy something. You’ve probably seen advertisements trying to exploit this vulnerability:
- “Offer valid only for the next 24 hours!”
- “Call now to get a 20% discount!”
Make no mistake, this is just as much social engineering as the above examples. Exploiting urgency can often multiply the chances of making the victim do something that they wouldn’t have done otherwise.
#4 Curiosity
The most obvious example of exploiting our curiosity is clickbait. You’ve definitely seen titles such as these:
- Top 5 things YOU NEED TO KNOW about [insert something useless]!
- You won’t believe what happened next!!
- #3 will blow your mind!
Most people will be aware that a 51 year old can’t just peel her face off and become 25 years old and yet we have this:

They’re not trying to be factually correct, they’re not even attempting to provide you any value. They have one goal, do whatever it takes to get you to click. And if the front page of websites like BuzzFeed or even YouTube is any indication, the effectiveness of clickbait is astounding. And this makes our curiosity one of the most exploited human traits of all.
Now let’s check out the next vulnerability. It will blow your mind.
#5 Sympathy
We might not think of sympathy as a weakness, but even when we’re at our most humble and kind, there are those who will try to exploit it. Here’s an example:
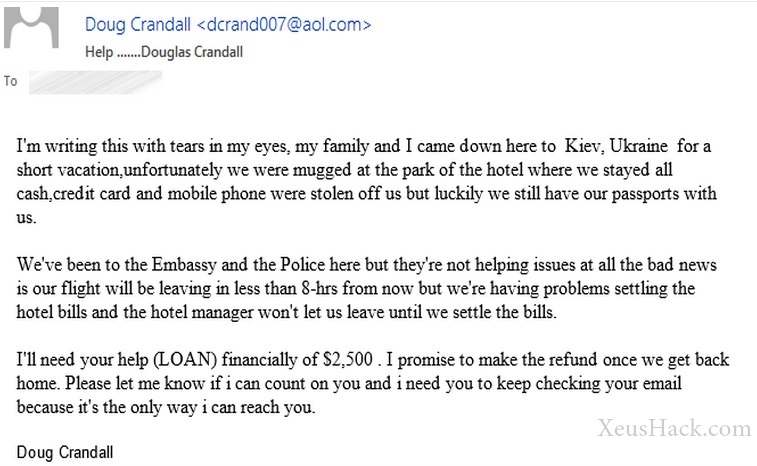
I assure you, the attacker definitely did not write this with tears in his eyes. Again, this type of attack is mainly targeted at the naïve, but it could be particularly dangerous if you see something like this coming from someone you know. If an attacker takes control of an email account, they’ll be able to send such emails to everyone in the victim’s contact list.
If you see the above email coming from someone you know, what would you do? When we see a message from a known person, we immedietaly let our guard down. We don’t expect our friends or colleagues to try to defraud and scam us. And this provides yet another vulnerability for an attacker to exploit.
#6 Respect for Authority
Your TV stops working. You call the TV guy. In a while, a person that looks like a TV guy shows up at your door. How often do people check their TV guy’s identification? (By the way, this is pretty much the plot of The Italian Job, a movie that draws heavily from social engineering)
When a person looks and acts in a specific manner, we automatically begin to form expectations, an image in our minds based on our past experiences. And this gives rise to yet another form of phishing:

Looks pretty convincing, doesn’t it? There are no obvious red flags here, the grammar, the logos, even an unsubscribe link- this could very well appear genuine to the untrained eye. Combined with the fact that most people probably don’t know what their local police department’s website URL is, this attack can prove to be quite dangerous.
#7 Inattention
Nearly all social engineering attacks can be defended against if only we remain constantly vigilant. Every single attack above relies on you not looking too closely at something, like the URL in a phishing attack. Even real-life scams and frauds count on you being ill-informed, inattentive and gullible.
Your browser might warn you if a website looks malicious, your email service might smartly put the most obvious attacks in your spam folder, but in the end, you stand alone. It is up to you to learn how to better protect yourself against whatever the internet (and beyond) can throw at you.
So these were the seven deadly sins of social engineering. By being aware of your weakness, you’ll be better able to defend yourself against all kinds of social engineering attacks. And now we’re going to learn how to carry out these attacks ourselves.
It’s time to pack your bags and head out because we are going on a trip. A phishing trip.
Want to be a real hacker? Sign Up!



